Information Security and Data Privacy Policies
Overview
At Sonata Software, safeguarding information, ensuring privacy, and maintaining resilient service delivery are central to our organizational values. The company has established a robust Integrated Management System (IMS) that unifies globally recognized ISO standards and embeds security, privacy, continuity, and IT service management into everyday operations.
Sonata Software’s (Sonata hereon) Integrated Management System (IMS) is aligned to leading industry standards—ISO 27001, ISO 27701, ISO 22301, ISO 20000-1, NIST, PCI, and SOC—to provide a robust, scalable, and consistent governance framework across the organization. This ensures continual improvement in:
- Information Security
- Data Privacy
- Business Continuity
- IT Service Management
The IMS enables Sonata to:
- Identify and manage security risks to information assets, regulation and privacy compliance, and service continuity
- Ensure consistent delivery of high-quality and resilient IT services
- Foster a culture of security and continual improvement
Complementing the IMS, Sonata has also established its Information Security Policy and Privacy Policy to safeguard information, manage risks, and ensure compliance with industry standards, regulatory requirements, and contractual obligations.
Scope of Sonata’s Policies
These policies apply to all employees, contractors, interns, business units, and third-party service providers who access or process Sonata’s information or IT assets. It covers all physical and digital environments, including on-premises systems, cloud platforms, mobile applications, and digital interfaces.
All users are required to follow these policies to ensure secure and compliant handling of information across Sonata and its subsidiaries.
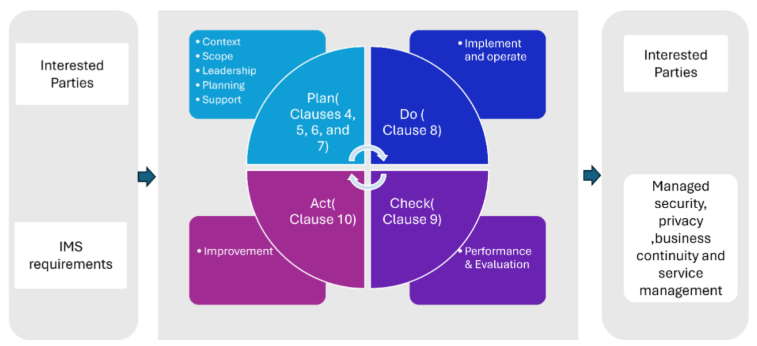
Approach & Methodology
Sonata adopts a harmonized approach to its IMS, integrating clause-level requirements across ISO 27001, ISO 27701, ISO 22301, ISO 20000-1, and ISO 9001.
Methodology for Integrated Management System
Integrated Management System Policy
Sonata is committed to safeguarding the confidentiality, integrity and availability of its company and clients’ data, intellectual property, and employees’ personal information at all times. It ensures uninterrupted business operations and compliance with our contractual, legal, and regulatory obligations.
Every employee, contractor, and stakeholder associated with our business is personally accountable and responsible for ensuring compliance with these objectives.
Lead by Example
Raise awareness, inspire others, and take decisive action to safeguard and enhance the security posture of data, information, intellectual property, and related assets. Continuously improve our practices in information security, privacy, business continuity, and IT service management.
Adopt a Zero Trust Security Framework
Assume no implicit trust and verify every access request continuously and rigorously, ensuring strict authentication and authorization for all users and devices. Protect data integrity and privacy through robust security controls and continuous monitoring to mitigate cybersecurity risks effectively.
Uphold Data Security and Privacy Standards
Adhere strictly to data security and privacy standards, ensuring compliance with all relevant privacy regulations and standards. Utilize company and client data, as well as intellectual property, solely for their intended purposes, accessing or managing data only with explicit authorization. Implement robust security controls, policies, and procedures to identify, protect, detect, respond to, and recover from cybersecurity risks, safeguarding both data integrity and privacy in accordance with local and international laws.
Ensure Resiliency
Establish and maintain comprehensive, adaptive strategies that safeguard our organization’s critical functions and services. This encompasses ensuring uninterrupted customer service, fortifying internal infrastructure, and implementing robust Business Continuity Plans (BCP).
Commit to Service Excellence
Implement efficient, adaptive processes and technologies that ensure the highest quality of IT services. This includes enhancing service delivery, improving incident response, and maintaining robust service continuity. By ensuring alignment with strategic goals, operational priorities, and customer expectations, we drive mutual success and satisfaction. Through continuous improvement, proactive monitoring, and stakeholder engagement, we aim to support our organization's goals and deliver exceptional value to our customers.
Stay Alert and Respond with Agility
Remain vigilant against potential threats such as ransomware or theft. Proactively prevent security breaches and minimize their impact if they occur, promptly reporting any security vulnerability, unusual behavior, or breaches for immediate action.
Sonata Information Security Policy
Sonata commits to ensuring:
- Information is accessed only by authorised users and systems.
- Information and services remain accurate, consistent, and reliable.
- Information and systems are accessible when required by business or clients.
- Personal data is processed fairly, lawfully, transparently, and securely.
- Services continue with minimal downtime during disruptions.
- All contractual, legal, regulatory, and stakeholder obligations are met.
- Proportionate controls based on risk assessment, threat intelligence, and business impact are applied.
- IMS – through monitoring, measurement, audits, and management reviews – are enhanced.
The IMS Policy is built on the following principles:
- Security by Design - Embed security, privacy, and continuity in all solutions, projects, and services from inception.
- Least Privilege & Zero Trust - Limit access to minimum required and continuously validate trust.
- Defence in Depth - Apply la`yered security across people, processes, and technology.
- Accountability & Traceability - Maintain clear ownership, audit trails, and evidence for all IMS activities.
- Stakeholder Assurance - Provide confidence to clients, regulators, and partners through transparency and assurance.
- Integration - Ensure information security, IT service management, privacy, and continuity objectives support each other within a unified IMS framework.
Sonata Privacy Policy
Sonata shall ensure the following commitments and practices are upheld:
- Data Collection and Processing
- For Employees (Controller Role): Sonata shall collect personal data exclusively for HR, payroll, and employee management purposes. The company will obtain explicit consent from employees before data collection.
- For Clients (Processor Role): Sonata shall process client data strictly according to the client’s instructions and contractual agreements, ensuring compliance with agreed-upon data processing terms.
- Sonata shall adhere to the following Privacy Principles, when processing Personal Information (PII, PCI, PHI)
- Lawfulness and Fairness: Sonata shall process all personal data in a lawful, fair, and transparent manner.
- Purpose Limitation: Sonata shall collect data only for specified, legitimate purposes.
- Data Minimization: Sonata shall collect and retain only the data necessary for the intended purposes.
- Accuracy: Sonata shall ensure that all personal data is accurate and up to date.
- Storage Limitation: Sonata shall retain personal data only for as long as necessary to fulfill its intended purposes.
- Security: Sonata shall protect personal data against unauthorized access, loss, or damage through appropriate security measures.
- Consent and Rights
- Consent: Sonata shall obtain explicit consent from data subjects before collecting their personal data.
- Rights of Data Subjects: Sonata shall respect and facilitate the rights of data subjects to access, rectify, erase, and restrict their personal data.
- Third-Party Management
- Vendor Management: Sonata shall ensure that vendors handling personal information undergo thorough security assessments and sign the necessary Data privacy agreements, to safeguard data privacy.
- Data Retention and Disposal
- Retention: Sonata shall retain personal data in compliance with legal requirements and dispose of it securely when it is no longer needed.
- Data Breach Management
- Reporting: Sonata shall promptly report any data breaches within required timeframes and notify affected parties as necessary to mitigate potential impacts.
- Compliance and Training
- Training: Sonata shall conduct regular training programs to ensure that staff are well informed about data privacy obligations and best practices.
The policy applies to data collected via automated means such as web analytics and cookies. This includes:
- Personal data collected directly by Sonata from employees, website visitors, vendors, and office visitors.
- Personal data collected as part of service delivery or operational functions by internal teams such as IT and Security.
- Personal data processed on behalf of clients who engage Sonata to provide services where Sonata acts as a Data Processor, and the respective client remains the Data Controller. In such cases, data is processed strictly in accordance with the client’s instructions, contractual agreements, and applicable data protection regulations (e.g., GDPR, DPDPA)
IMS Governance
Sonata’s Information Security Management Program is led by the Chief Information Security Officer (CISO), who is responsible for strategic oversight and governance of:
- Information Security
- Data Privacy
- Business Continuity
- Security Risk Management
The CISO ensures that Sonata maintains a strong security posture through risk-based controls, continuous monitoring, audit readiness, and stakeholder assurance.
A dedicated security governance structure supports the CISO, including domain experts for cybersecurity, privacy, business continuity, and service management, ensuring end-to-end compliance and operational effectiveness.
The program ensures:
- Risk-based controls aligned to industry standards
- Robust governance and periodic reviews
- Incident management and continual monitoring
- Independent audits and surveillance assessments
- Transparent reporting to stakeholders and clients
Conclusion
Sonata is committed to delivering secure, reliable, and privacy-centric services to all clients worldwide. Through a unified Integrated Management System and adherence to global standards, Sonata ensures the continual protection of information assets, resilient operations, and consistent service excellence.

